How to generate Azure application credentials manually
Create Azure application
- Open Azure portal and click on Microsoft Entra ID.

- Select App registrations from the left menu and click on New registration.

- Enter the name of the new application and provide redirect URI as https://localhost

Assign API permissions
- Click Manifest from the left pane.
- Look for the requiredResourceAccess array in the code.
- Copy the entire contents from this file and paste them into the section highlighted in the image below.
Note:
- If your tenant is being created in Azure Germany, copy the entire contents from this file and paste them into the section highlighted in the image below.
- If your tenant is being created in Azure China, copy the entire contents from this file and paste them into the section highlighted in the image below.
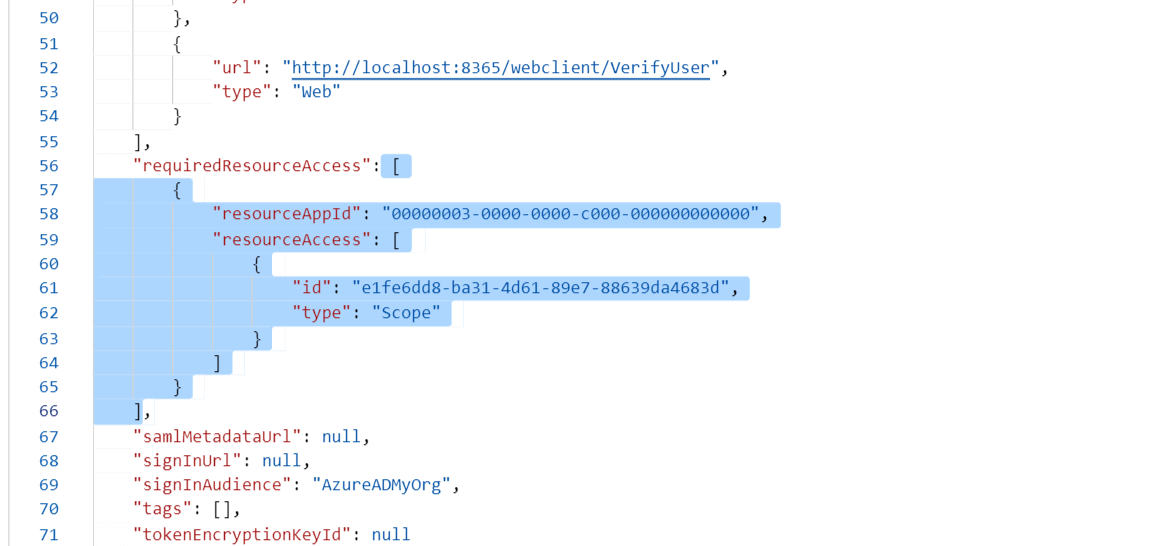
- Copy-paste content only from the open square bracket to the closed square bracket. Ensure that all punctuation marks are retained correctly. Once you have pasted the file, it should look like the image below.

- Click Save.
- Navigate to API Permissions from the left pane. Click on Grant admin consent for <your_company>

Create client secret and upload certificate
- Open Certificates & secrets and click on New client secret from Client secrets tab. Note down the generated client secret.

- Open PowerShell as administrator in the <product folder>/conf. Replace <Your-Company-Name> in the below query and execute. Please note down the certificate password.
.\Create-SelfSignedCertificate.ps1 -CommonName "<Your-Company-Name>" -StartDate (Get-Date).ToString("yyyy-MM-dd") -EndDate (Get-Date).AddYears(4).ToString("yyyy-MM-dd")

- Two files, in .cer and .pfx format,will be created at the script location. Upload the .cer file to the azure portal as shown in the below image. The .pfx file will be used in the product later.

Configure Microsoft 365 tenant in SharePoint Manager Plus
In SharePoint Manager Plus, use Azure application authentication and enter Tenant Name, Application Id, Secret key, complete location of generated .pfx certificate file and certificate password to configure the tenant.

Note: Please provide the complete path of certificate location in the configuration. (e.g) C:\Program Files\ManageEngine\SharePoint Manager Plus\conf\ZohoCorp.pfx
You can find the Application ID in the Overview tab.

How to find tenant name?
- Open Azure Portal home page
- Navigate to Microsoft Entra ID ⟶ Custom domain names.
- Select every domain and check if it is Initial.
- Use the initial domain as the Organization Name in SharePoint Manager Plus.














